Windows Driver Signing - Introduction
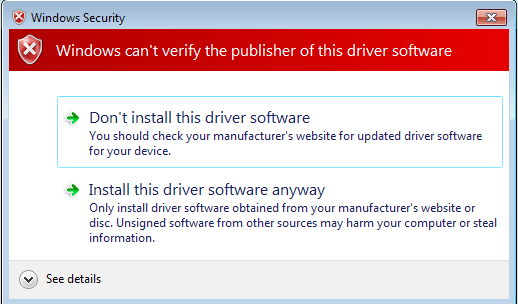
Code signing is the process of digitally signing your code to confirm the software publisher and guarantee that the code has not been changed since it was signed by the publisher. To be more specific, a signed driver is a driver sealed with a digital signature, which assures that the original contents of the driver package have not been altered since the driver was signed by a publisher that has verified its identity with a certification authority. This helps users determine whether the software can or cannot be trusted. If a driver is unsigned, or signed by an unknown publisher, Windows will alert the user with a pop-up message like the one below.
Windows Driver Signing - Synopsis
- Obtain a code signing certificate.
- Download and install the necessary tools.
- Generate the .cat file.
- Download the Cross-Signing certificate.
- Sign and timestamp the driver.
- Verify the driver’s signature.
Windows Driver Signing - Analysis
Obtain a code signing certificate.
The first thing you need to do before starting the driver’s signing process is choose a certificate issuer and purchase a code signing certificate. Digital certificates allow developers to digitally sign code in order to prove that it has not been altered by a third party, as well as prevent the annoying warning messages that appear during a program’s installation. For drivers signing, codebender uses an Extended Validation (EV) Code Signing Certificate provided by Digicert.
Download and install the necessary tools.
After you’ve obtained the certificate, you will need two tools that will help you during the driver signing process: SignTool and Inf2Cat. Inf2Cat will be used to generate the security catalog file (.cat file), while SignTool will be used to sign it. Inf2Cat tool is provided by Microsoft via the Windows Driver Kit (WDK), and SignTool can be obtained through the Windows Software Development Kit. Some versions of the Windows SDK are included in Visual Studio installation.
Generate the .cat file.
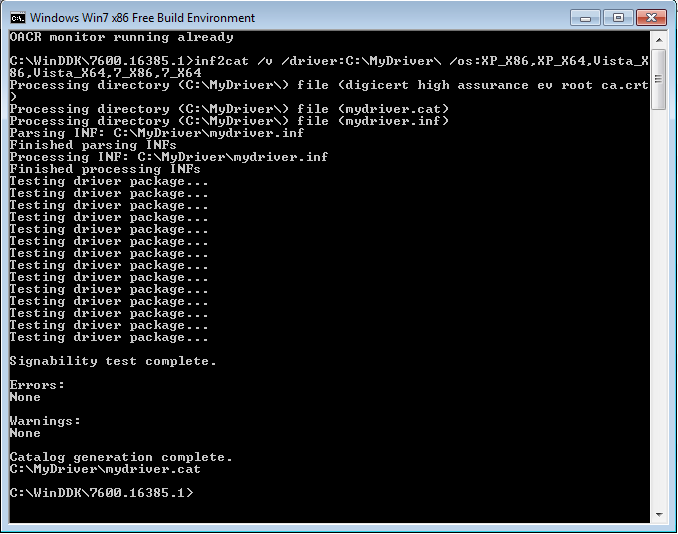
Once you have obtained the certificate and installed the tools, you are ready to create the .cat file for your driver using the Inf2Cat tool. Navigate to C:\ , create a folder (e.g MyDriver) and copy your .inf file inside.
Open x86 Free Build Environment by navigating to Windows Driver Kits, WDK YourBuildNumber,Build Environments, Windows 7, and clicking on x86 Free Build Environment.
Run the command:
inf2cat /v /driver:C:\MyDriver\ /os:XP_X86,XP_X64,Vista_X86,Vista_X64,7_X86,7_X64
Syntax:
inf2cat /v /driver:path /os:os1,os2,...
/v: Configures inf2cat to display verbose information in a command window.
/driver:path: Path to the directory that contains the .inf file.
/os:os1os2,...: Configures inf2cat to verify that a driver's .inf file complies with the signing requirements for the Windows versions that are specified by WindowsVersionList.
If the catalog generation was successful you will be able to see the message: Catalog generation complete. and mydriver.cat file will appear inside C:\MyDriver\ directory.
Download the Cross-Signing certificate.
In order to be able to use SignΤool and sign your driver, you will need to download and copy your CA’s Code Signing Cross-Certificate on the folder where your .cat file is located. You will need to specify this certificate in SignΤool. Microsoft provides a list of cross-signing certificates they currently support, which the developer can download and use during the signing process.
Sign and timestamp the driver.
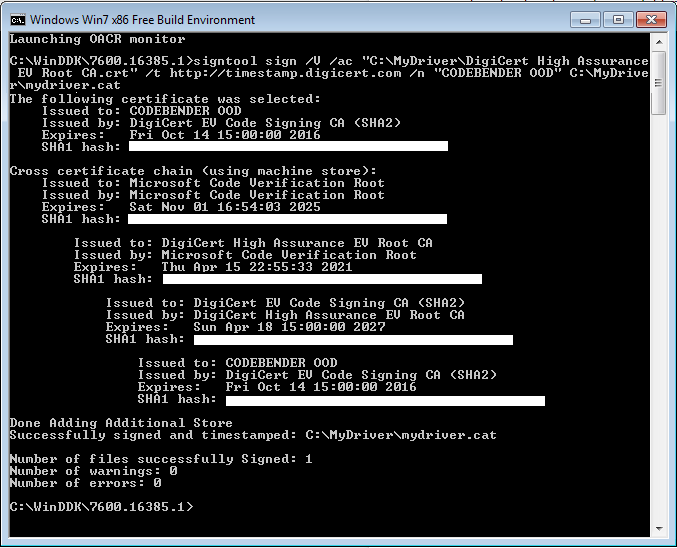
Once the catalog file generation is completed, you will finally be able to sign and timestamp your driver. It is important to timestamp your signatures so that they will continue to work after your certificate’s expiration. To timestamp your signature, you will have to include an argument of the form /t https://timestampserver/ when you invoke SignTool.
To sign your .inf file run the command:
signtool sign /V /ac "C:\MyDriver\DigiCert High Assurance EV Root CA.crt" /t https://timestamp.digicert.com /n "CODEBENDER OOD" C:MyDriver\mydriver.cat
Syntax: signtool sign /V /ac "cross-signing-certificate" /t URL /n "subject-certificate-name" catFile
sign: Command used to sign files.
/ac "cross-signing-certificate": The cross-signing certificate downloaded previously.
/V: Configures signtool to display verbose information in a command window.
/t URL: Specifies the URL of the timestamp server.
/n "subject-certificate-name": Specifies the name of the subject of the signing certificate.
catFile: The catalog file that you want to sign.
Verify the driver’s signature.
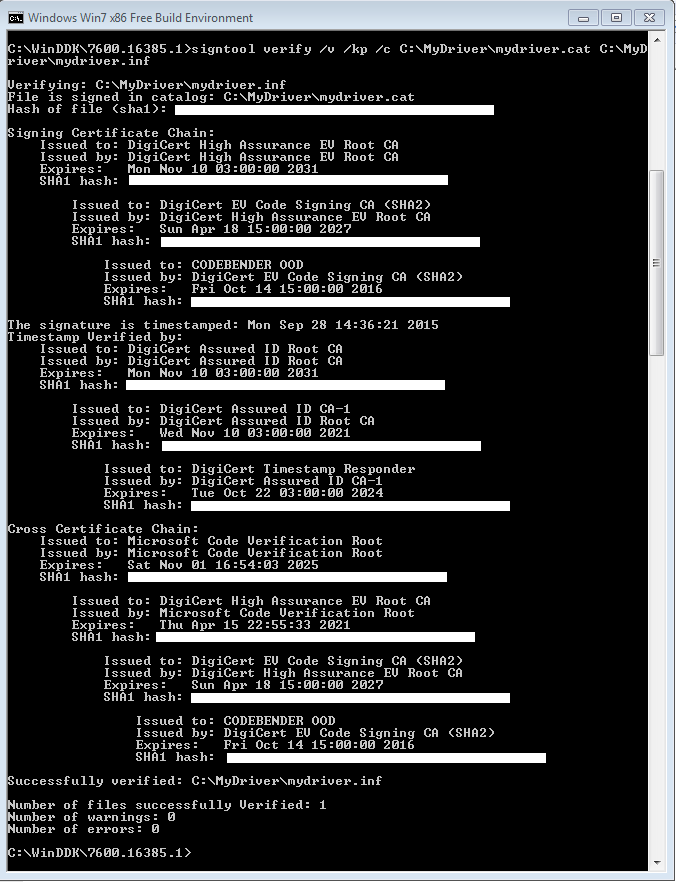
To verify that your cat file was successfully signed you can use the following command:
signtool verify /v /kp /c C:\MyDriver\mydriver.cat
The verify command configures SignTool to verify the signature that is embedded in the catalog file.
Syntax: signtool verify /v /kp /c catFile
verify: Command used to verify signature. /v: Configures signtool to display verbose information in a command window.
/kp: Configures SignTool to perform the verification by using the x64 kernel-mode driver signing policy.
/c catFile: Specifies the catalog file by name.
I hope that you have enjoyed reading my post!